About SSH Keys
On IPSL mesocenter , ssh remote login is only allowed with RSA key ( no password )
It's not possible to add unknown keys from central management in your authorized_keys on the mesocenter (automatically removed)
Access via SSH to head nodes is worldwide open on internet
What is key authentication over SSH protocol ?
SSH key authentication is an alternative security method to using passwords, simpler than it sounds.
- This method relies on generating a pair of files as known as "SSH key pair". Basically, everything encrypted using one of the file/key can be decoded by the other one.
- One file is called "the public key" and can be seen as simple lock.
- Second file is called "the private key" and can be seen as the corresponding lock key.
-
Once you generated such a key pair on your local machine (e.g. your laptop), we install the public one on the IPSL clusters as a door lock that can be opened by your "private key" only when you run SSH connexion.
- Consequently your private key must be on the computer you are connecting from.
- Your private key need to be secret (as any of your passwords). To do so, your private key should be itself protected with a password or a passphrase, which only you know, as it was securely stored in a vault.
-
In the case you forget the password/passphrase or lose your private key, the whole key pair has to be changed in the same way that you lose your home key. Obviously we would like to avoid changing many locks a week, we highly recommend to DUPLICATE your key pair in a safe place:
- copy on another machine (another server in your lab/university/... is a good destination )
- private or even public cloud if your key is secured with a password/passphrase.
-
Finally, having several locks per door is not necessary which means multiplying the number of key pair per users.
Generating your key with ssh-keygen on linux or MacOS
- keep filename by default when generating : just type return for Enter file in which to save the key (30% of problem)
- always protect your key with a passphrase (do not forget it : 10% problems https://keepassxc.org/)
- Really put your ssh public key in good form in the Account form 50% problems
a private key (identification) could be easily copied from one computer to another
The best thing is to generate the key on one of your laboratory UNIX/Linux server
even to use with linux,MacOS or windows laptop after.
like this you have a copy of your private key and you could continue
to connect even if you lost or broke your laptop
terminal command to use to generate the key :
ssh-keygen -b 4096 -t rsa
full sample of keys generation
[user@localhost ~]$ ssh-keygen -b 4096 -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
Enter passphrase (empty for no passphrase): *******************
Enter same passphrase again: *******************
Your identification has been saved in /home/user/.ssh/id_rsa.
Your public key has been saved in /home/user/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:tpdrIr1dW5uCKr6AvCu/GXdauBvOY4nqENGK+aGWoU0 user@localhost
The key's randomart image is:
+---[RSA 4096]----+
| |
| . |
|. . |
|.+ |
|=.E S |
|.Boo . . . . |
|+o*.=.o.. o.. . |
|+ .B+Bo oooo.o o |
|o=*+*+o+o=o ..o |
+----[SHA256]-----+
[user@localhost ~] cat /home/user/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMW7eR0JPEh/1F4k2LEoBQMHaZ3uRL6uZM3S9LEzwhXKnOwpjP3opsjldCgyc3xSTbrgWCoJLdq4xitTmLF/1Da6a3CX9PHLB3WT0YeJCa2vGbHozqldgDg4k8ZagaYFozK7uMqeZTYdhPN2Q9YE+ptaXFUXMyOaUbfSuMPMyHeAc7MeG7f+ivf4RunQTcnY8fbLM2Gx1voE5KUTph1atRgkOKYmNSWPijn2qmQ6BYeFwttojiuOWH0bCSXy/JywinamyBzt0JK40rAlCa09lP+5jia0N0Sn6nmijZ1o3oaO6nOjYMZ1os3OAbmafX8wfSDarKqWE5kQQmF5abyZ9PvI+MliXVe//bEjIxW00z0s3bM6EWzJ1/MmtI5aNT3DpgXx0pzh9uPMA5tgdl90BvxXNljovxriYqtwcWTfWtEDnQekFOeQI3S/ou0rRZ80n3RwUTs0soxkOo4lSTP2Jh/KYeGqQPuMPOLiW5oHZPXQZ5uu0VWCjFB9kD+NXxoWoOrJ6t6DRzwoEO83V87uUyz3Bzlw9aixxWEr38CW7ZVXqpTnFKj/TdPkny7Ms77cLBb3WbPZTWmJlO9MNNPGFuoHWRR/n199BYSRu46Zvh0k2xivJ52JdJ/ud0DfRY0p4CoAWupNaMw0qRDUzawkY+pKVHTf2oJF7KuTZhabuXmQ== user@localhost
The ssh public key needed in the form is only this under
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMW7eR0JPEh/1F4k2LEoBQMHaZ3uRL6uZM3S9LEzwhXKnOwpjP3opsjldCgyc3xSTbrgWCoJLdq4xitTmLF/1Da6a3CX9PHLB3WT0YeJCa2vGbHozqldgDg4k8ZagaYFozK7uMqeZTYdhPN2Q9YE+ptaXFUXMyOaUbfSuMPMyHeAc7MeG7f+ivf4RunQTcnY8fbLM2Gx1voE5KUTph1atRgkOKYmNSWPijn2qmQ6BYeFwttojiuOWH0bCSXy/JywinamyBzt0JK40rAlCa09lP+5jia0N0Sn6nmijZ1o3oaO6nOjYMZ1os3OAbmafX8wfSDarKqWE5kQQmF5abyZ9PvI+MliXVe//bEjIxW00z0s3bM6EWzJ1/MmtI5aNT3DpgXx0pzh9uPMA5tgdl90BvxXNljovxriYqtwcWTfWtEDnQekFOeQI3S/ou0rRZ80n3RwUTs0soxkOo4lSTP2Jh/KYeGqQPuMPOLiW5oHZPXQZ5uu0VWCjFB9kD+NXxoWoOrJ6t6DRzwoEO83V87uUyz3Bzlw9aixxWEr38CW7ZVXqpTnFKj/TdPkny7Ms77cLBb3WbPZTWmJlO9MNNPGFuoHWRR/n199BYSRu46Zvh0k2xivJ52JdJ/ud0DfRY0p4CoAWupNaMw0qRDUzawkY+pKVHTf2oJF7KuTZhabuXmQ== user@localhost
Generating your key on Windows
if you don't have mobaxterm you could download Mobaxterm : https://mobaxterm.mobatek.net/download-home-edition.html choose the portable edition ( this version is just one binary and install nothing on your windows computer ) use mobaxterm to generate your keys
launch the mobaxterm application
- click to tool
-
then select mobakeygen menu
-
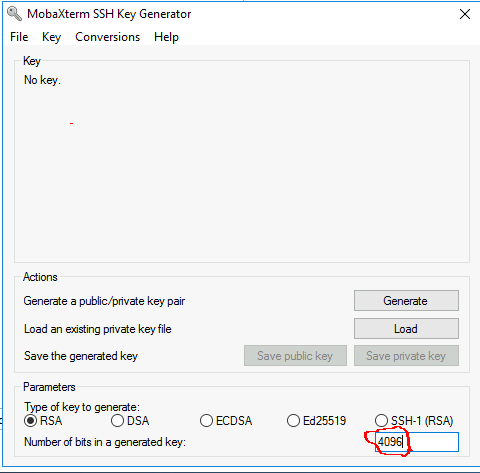
choose RSA
- in " number of bits in a generated key " : put 4096
- click on generate then move the mouse as asked
at the end you obtain this
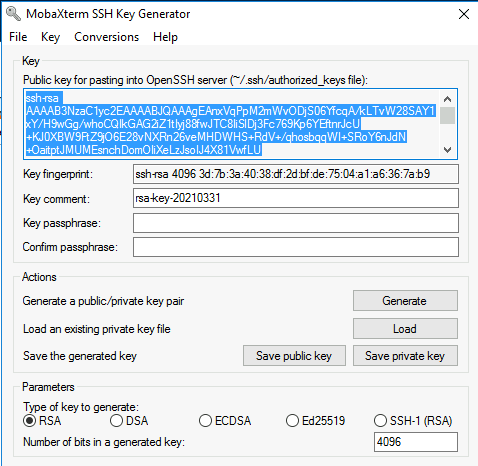
- protect your key with a passphrase
- confirm the passpahrase
- click on save private key
- put on the desk with name "meso_rsa"
you see only a parts of the key in the blue window : to get all the key, you need to use Ctrl A Ctrl C to select all the text in the blue window then use CTRL V to put the key in the form. the key must finish by rsa-key-yyyymmdd
You need now to import your new key in mobaxterm
Import key in Windows mobaxterm
- click to Settings
- select SSH tab
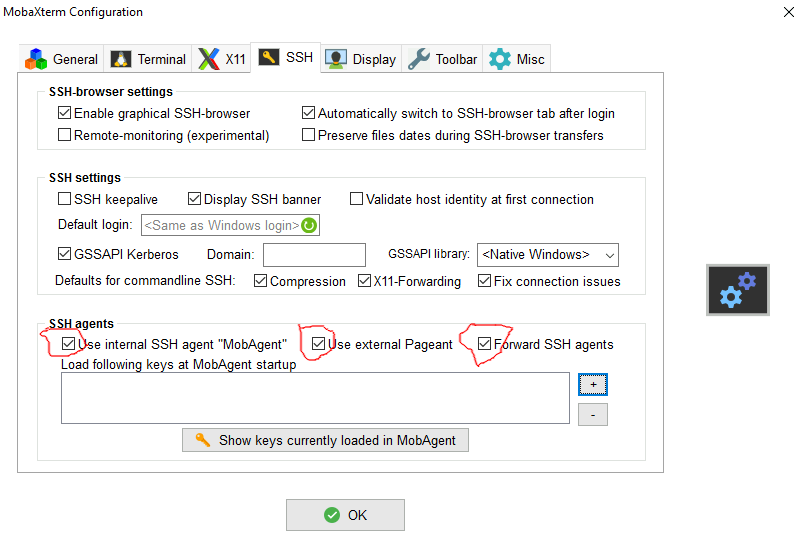
- Activate the 3 options :
- "X" Use Internal SSH Agent
- "X" Use External Pageant
- "X" Forward Agent
- click on the + sign to import your private key ( meso_rsa or id_rsa file)
you should have something like this after
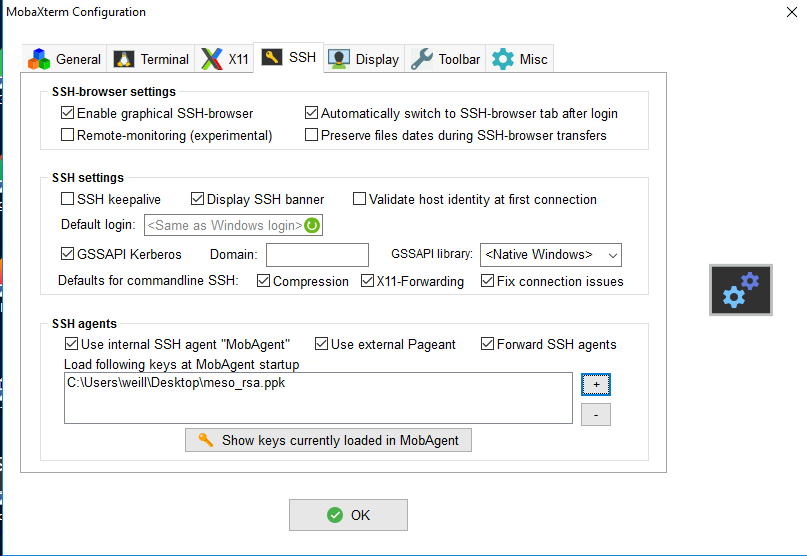
- click on OK
- quit mobaxterm then restart mobaxterm
You're now ready to test the connection to the mesocenter (if your account is already open)
SSH Connection to ipsl mesocenter has never work , what to do ?
- See with your local system administrator and show him this documentation
- cut and past the following command in a terminal on the same machine you generate the key (Linux/MacOS/Windows(MobaXterm))
uname -a;ls -al $HOME/.ssh;ssh-add -l;ssh-add -L;head -2 $HOME/.ssh/id_rsa;cat $HOME/.ssh/id_rsa.pub;date;
ssh -vvv replace_by_your_login@ciclad.ipsl.jussieu.fr - send all the text written to the terminal by mail (please no screen copy image):
to mailto:meso-support@ipsl.fr
with subject : ssh first connexion problem for login 'your login on IPSL mesocenter'
I want to access from another computer
Linux/MacOS
you just have to copy the file $HOME/.ssh/id_rsa from the already working computer
to the new computer in $HOME/.ssh/id_rsa
after the copy, type following command on the new computer
chmod 600 $HOME/.ssh/id_rsa
Windows
we recommand to use Mobaxterm : https://mobaxterm.mobatek.net/download-home-edition.html choose the portable edition ( this version is just one binary and install nothing on your windows computer )
If your working computer is :
- Linux or Mac : you need to copy the file
$HOME/.ssh/id_rsa( the Private Key ) from the already working computer to your windows computer - Windows : you need a copy of your Private Key (.ppk ) from the already working Windows computer
and see importing key in Windows mobaxterm
Using config file on Linux or MacOS
With ssh you could create the file $HOME/.ssh/config to simplify some ssh setup
- fixing some options
- fixing remote username for one host
- using host alias
sample :
[user@localhost ~]$ cat $HOME/.ssh/config
# to know more about config file
# man ssh_config
#
ForwardX11 yes
# equivalent to -X on command line
ForwardAgent yes
# equivalent to -A on command line
ServerAliveInterval 90s
# for dying ssh connections
ForwardX11Timeout 168h
# X11 stop working after sometime like 20 minutes on some MacOS version
HostkeyAlgorithms +ssh-rsa
PubkeyAcceptedAlgorithms +ssh-rsa
# recent Linux (fedora 33/34, arch , manjaro, ubuntu 21.04 ) with openssh 8.8
# have RSA deactived by default , use above to reactivate
# equivalent to -o HostkeyAlgorithms +ssh-rsa -o PubkeyAcceptedAlgorithms +ssh-rsa on command line
#
# climserv is just an alias but could be use like this
# ssh climserv is equivalent to do ssh foobar@camelot.ipsl.polytechnique.fr
Host climserv
User foobar
Hostname camelot.ipsl.polytechnique.fr
[user@localhost ~]
Other example:
Info
Replace <login_ciclad>, <login_jean_zay> and <path_to_ssh_key> with your own login/path.
Host ciclad
HostName ciclad-ng.ipsl.upmc.fr
User <login_ciclad> # replace with your own login
ForwardX11 yes
IdentityFile <path_to_ssh_key> # replace with your own path, e.g. ~/.ssh/id_rsa
Port 22
Host jean-zay
HostName jean-zay.idris.fr
User <login_jean_zay> # replace with your own login
IdentityFile <path_to_ssh_key> # replace with your own path, e.g. ~/.ssh/id_rsa
Port 22
ProxyCommand ssh ciclad -W %h:%p # proxy jumping with ciclad